Do You Really Need Dark Web Monitoring?
The dark web represents a hidden segment of the internet that is inaccessible via traditional search engines like Google. Special software is...
3 min read
![]() Totalcare IT
:
Jan 23, 2023 10:04:16 AM
Totalcare IT
:
Jan 23, 2023 10:04:16 AM
When your personally identifiable information (PII) is exposed in a data breach, the authorities may ultimately recommend (after many other steps) that you use credit monitoring services. Of course, you should only do so when recommended by your IT team, the police and your insurance company. Nevertheless, these services are useful to those who take advantage; they can keep an eye out for suspicious use of your identity or financial information, which is useful when your PII might have been exposed in a breach. Have you ever gotten an email like this?
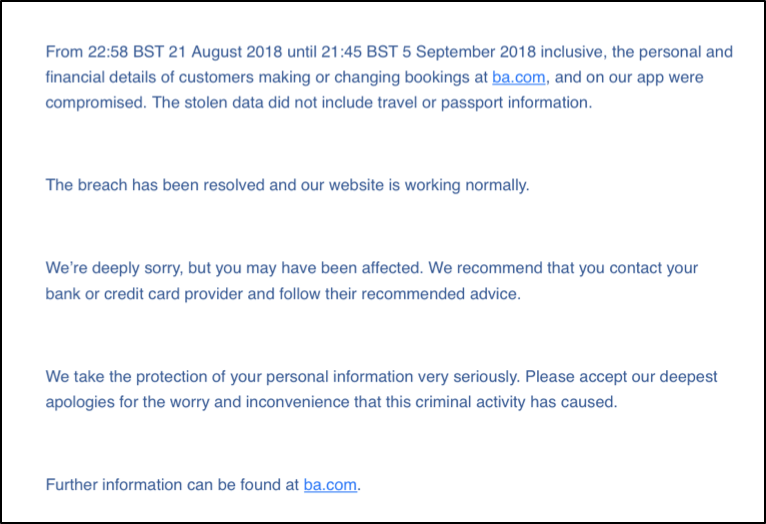
You’ll receive a similar message when a company to whom you’ve entrusted private data experiences a cyber event that exposes the PII of their customers, but they’re not completely sure whose information was seen or stolen. Therefore, they might recommend that everyone take precautionary steps to re-secure their data and monitor their accounts for fraud moving forward. That often includes credit report monitoring services that detect suspicious charges given your credit history.
What do you do when the credit monitoring company is the one that got hacked, and whose database was exposed?
TransUnion Data Breach
Unfortunately, that exact scenario happened to people doing business with TransUnion. The American-based consumer credit reporting agency maintains data for over 500M businesses, and more than 1 billion individuals worldwide! 200 million of those customers hail from the United States.
Unfortunately, some of them also had their names, Social Security Numbers, financial details, and driver’s licenses exposed in the attack. Although the company has not disclosed how many customers’ PII was affected, TransUnion notified people via letter about the exposure. They’ve also relayed it to the Massachusetts Attorney General.
You may remember a similar incident occurring at Equifax back in 2017. At the time of that data breach, some 147 million people’s data was exposed and the company entered a settlement agreement with the FTC to the tune of $425M. This payout was distributed to individual victims to help cover their losses, recovery fees, and other expenses resulting from the breach, including time spent addressing identity theft. Yep, that can happen too!
While TransUnion customers should wait for officials and authorities to address the next steps, they can look to past cyber events for an idea of what to expect next.
Are Credit Card Monitoring Services Safe?
Data breaches like these create ironic conundrums; how can we trust someone to monitor our credit history and identity, if that’s the industry that affected us in the first place?
That’s something only your research and overall cybersecurity posture can answer. When you sign up with credit monitoring services, you can and should ask them questions about what protections they put in place to safeguard the data in their care. That includes digital encryption AND physical barriers to outside eyes! Simultaneously, the overarching security protections placed on your systems need to be up to par. Services like Dark Web Monitoring instantly notify you of PII found up for illegal sale. This will provide an additional eye out in case one of your other services falls victim to an attack.
By the way, more than three-fifths of small- to medium-sized businesses experience cyber-attacks every year. We know that phishing and ransomware attacks, some of the most dangerous kinds that we face, are on the rise. Not only are cyber-attacks unfortunately common occurrences, but the epidemic is getting worse.
Do your part by paying attention to blog articles like these, as well as brushing up on your Security Awareness Training throughout the year. Did you know 95% of data breaches involve human error? Let’s all do our part to bring that number down, and cyberattacks could plummet!
Unfortunately, credit report monitoring services are just as susceptible to hackers as any other business. Given the nature of the PII they collect, they’re a natural target for cybercriminals looking to commit financial and identity theft. However, they should not be your only source of PII monitoring and protection.
Data protection is an ongoing effort in the war against cybercriminals! Vigilance is key, and becoming better informed about who is protecting your data and how they do so are both crucial steps to staying secure on a daily basis. So is keeping up to date with the latest tips and tricks in the industry. Schedule a 15-minute, no-obligation conversation with our team to learn more.

The dark web represents a hidden segment of the internet that is inaccessible via traditional search engines like Google. Special software is...
Imagine this: you leave your house for vacation. You live in a shady neighborhood but feel confident your locks are secure. But you also don’t check...

You’re the captain of your own ship. Your crew, a team of hardworking employees, rely on your vessel’s technology to help navigate the stormy waters...