2 min read
TotalCare IT Blog
Knowledge articles for Idaho business leaders on technology, cybersecurity, and compliance.
Cybersecurity (11)
3 min read
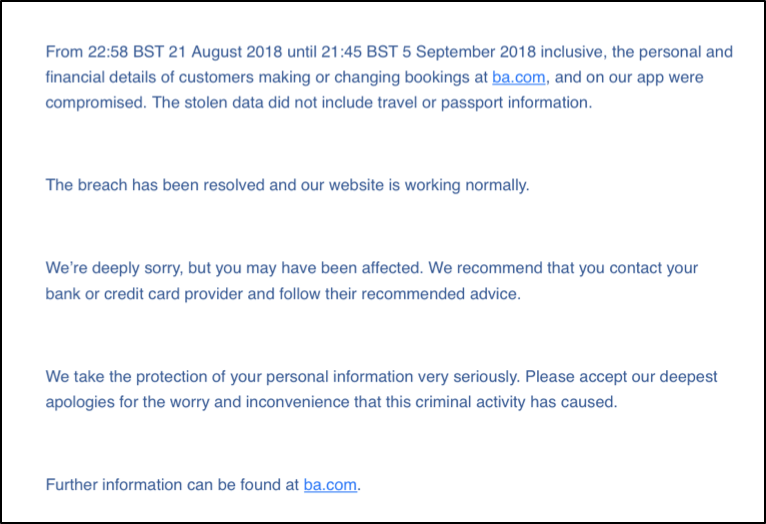
When Credit Card Monitoring is Illegally Monitored
3 min read
What Cybersecurity Attack Trends Should You Watch Out for in 2023?

4 min read
Seven Ways to Maximize Cloud Solutions for Your Small Business

3 min read
What Is Microsoft Defender for Individuals & What Does It Do

3 min read
Simple Guide to Follow for Better Endpoint Protection

3 min read
What Are the Most Helpful VoIP Features for Small Businesses?

3 min read
Don't Set Yourself Up to Fail: Tips for Safer Home Security Setups

3 min read




